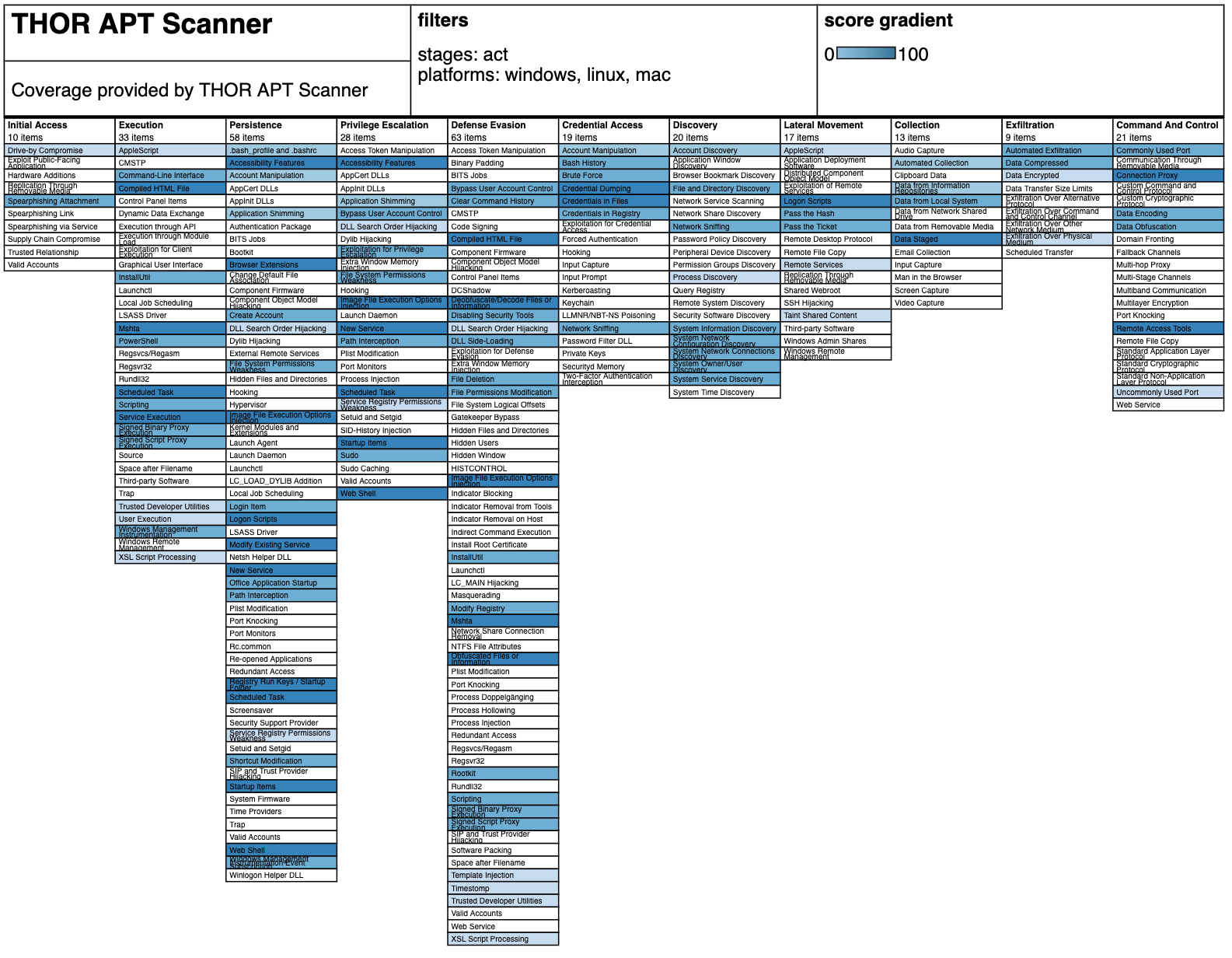
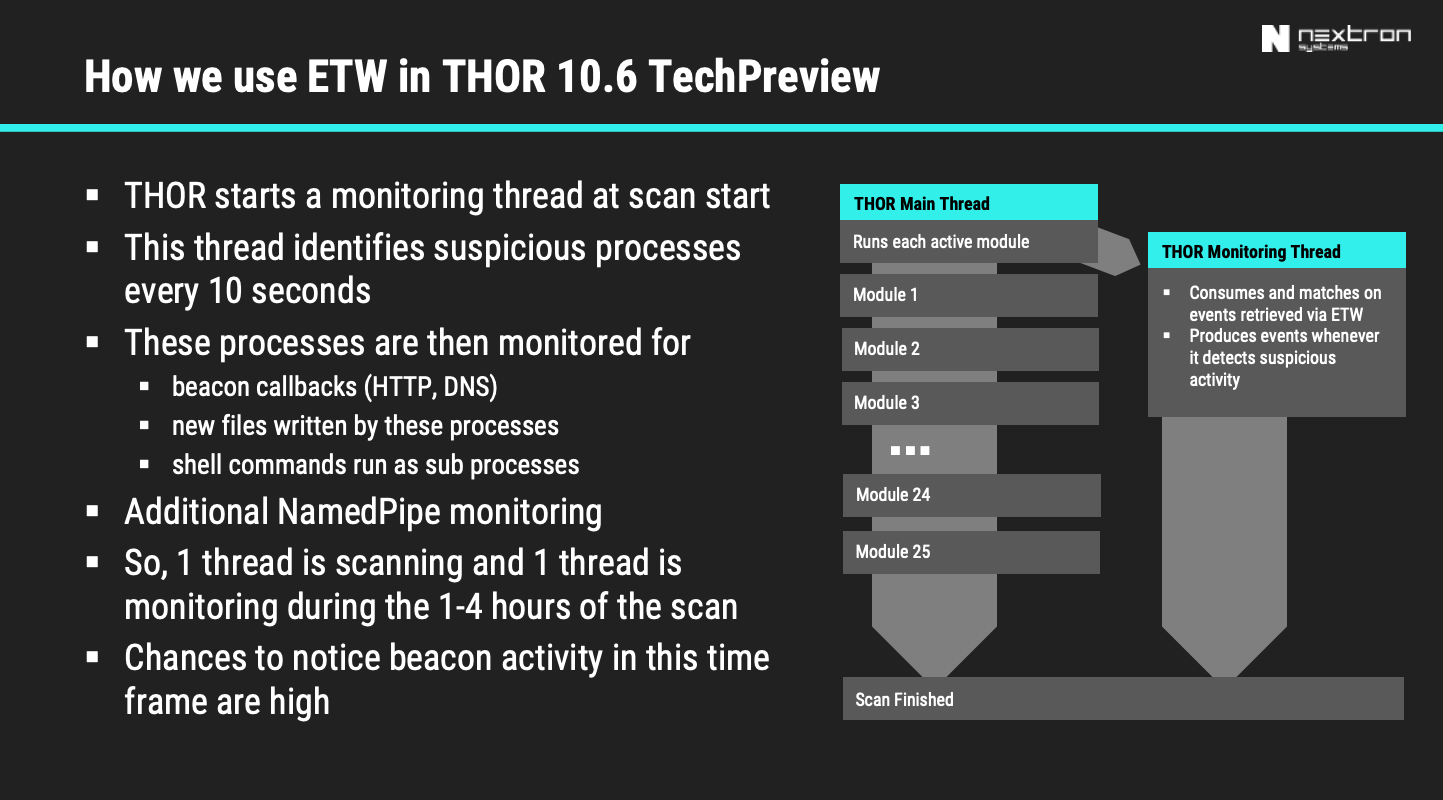
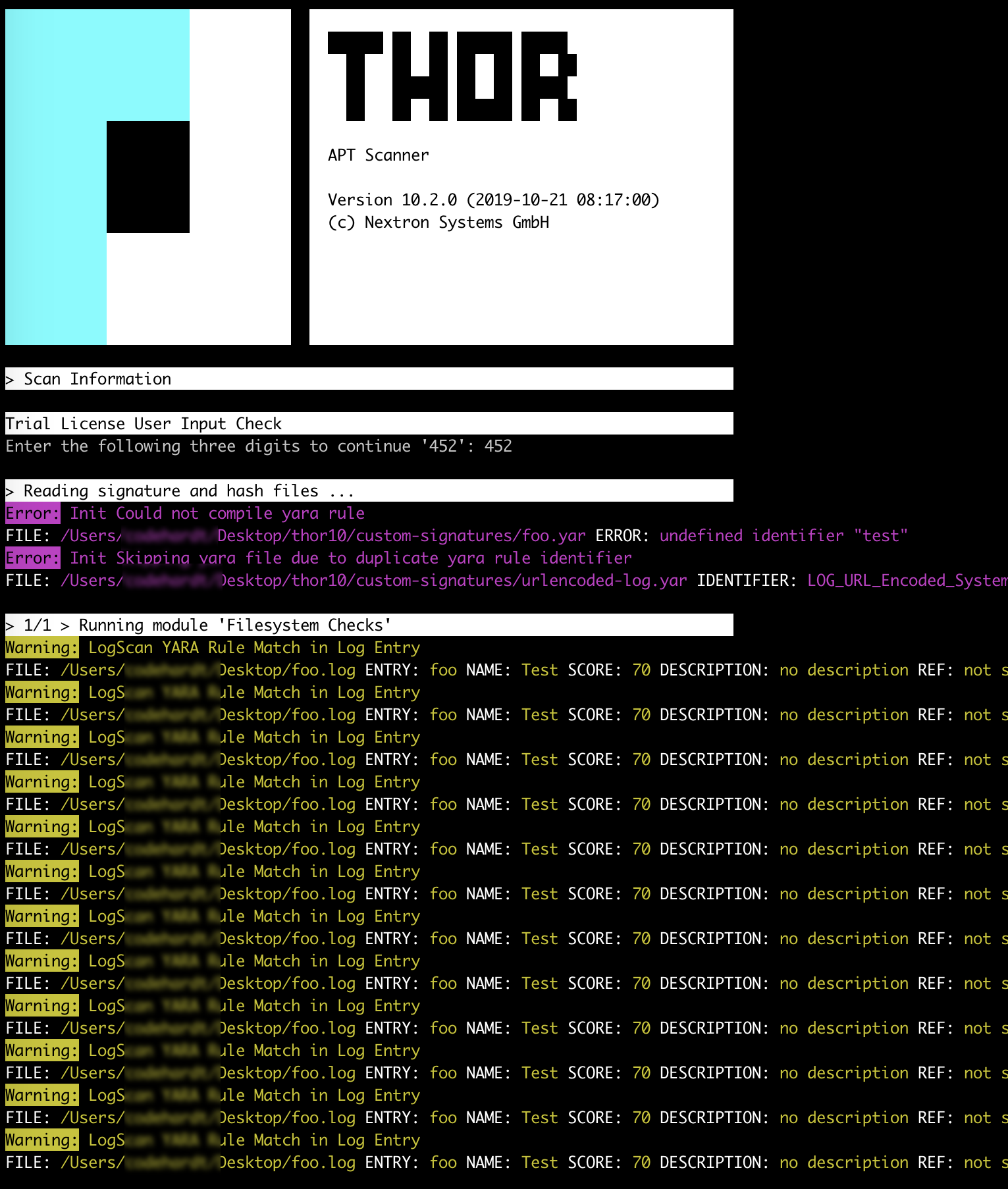
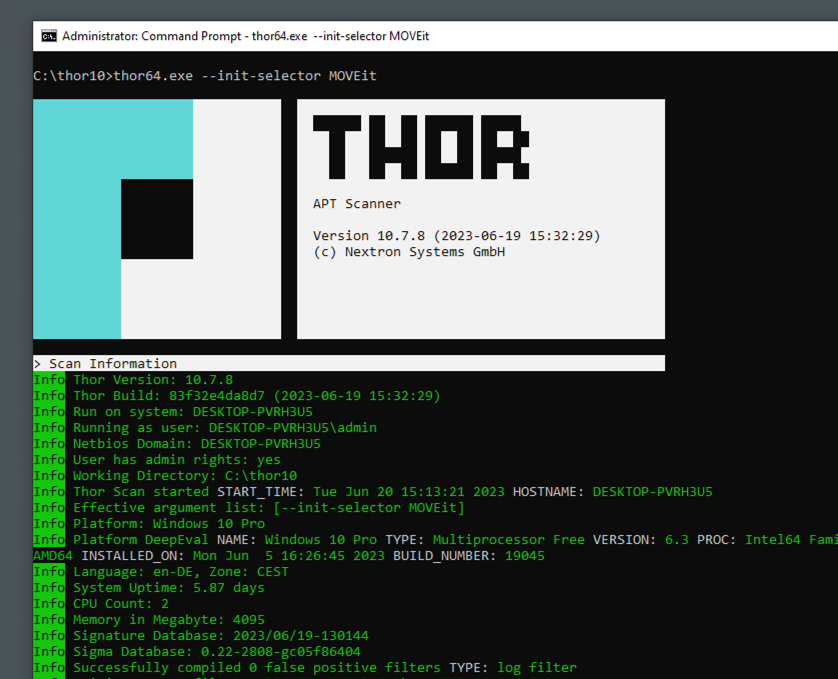
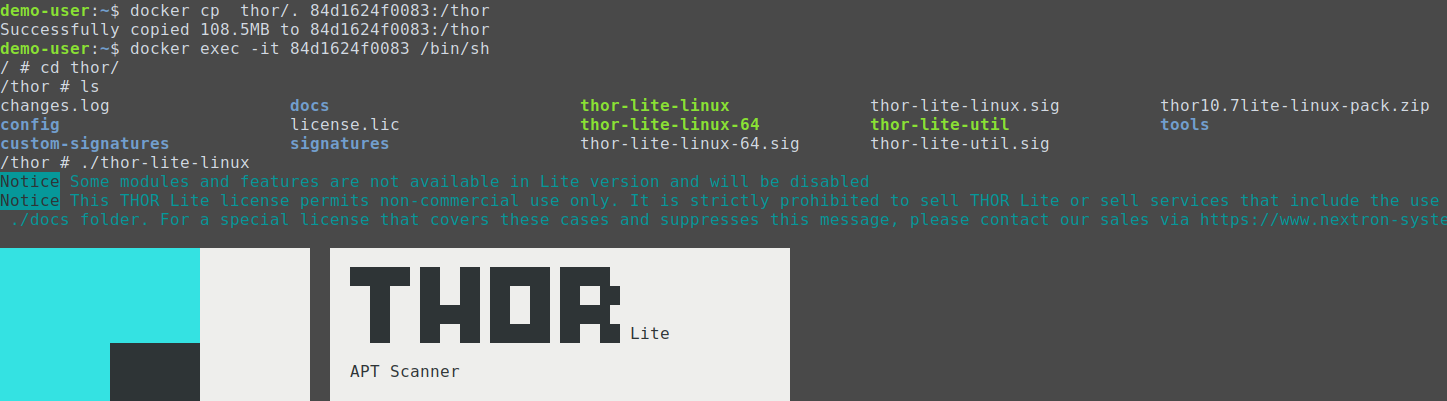
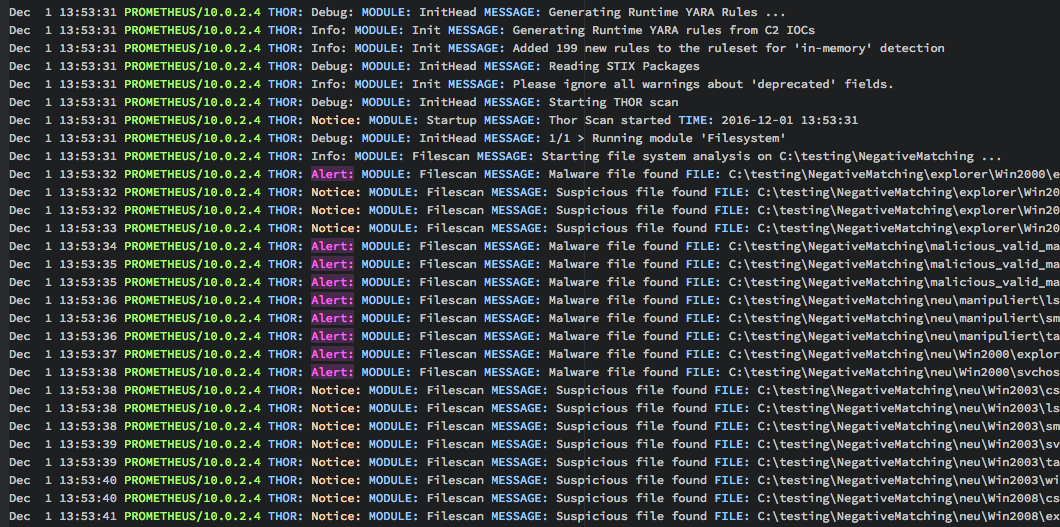
How to scan systems with THOR lite scanner during compromise assessment and incident response | by Md. Mahim Bin Firoj | Medium

Nextron Systems on X: "THOR APT Scanner Registry Detection Examples - malware, manipulations, cache entries, backdoors, anomalies #DFIR #APT http://t.co/31lIk2GFH2" / X